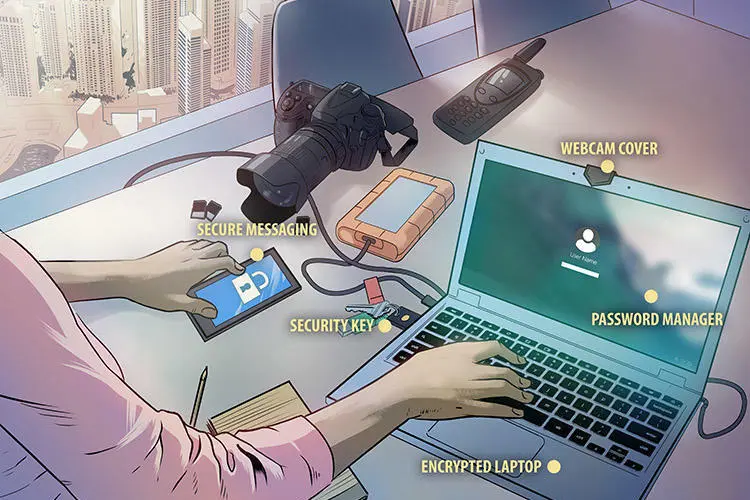
Journalists face a wide range of digital threats and it’s increasingly important that they protect themselves and their sources by keeping up to date on the latest digital security news and threats such as hacking, phishing, and surveillance. Journalists should think about the information they are responsible for and what could happen if it falls into the wrong hands, and take measures to defend their accounts, devices, communications, and online activity.
This digital safety kit is designed to be a general starting point for journalists looking to increase their digital safety. For more detailed security advice, please see our Safety Notes. Journalists are encouraged to complete a risk assessment before starting their assignments.
Contents
Protect against targeted phishing attacks
Protect your online data
Journalists are increasingly targeted by online abusers who comb the internet looking for personal data that can be used to threaten and intimidate them. Journalists are advised to review their online profile regularly and take steps to remove information where possible.
To better secure your online data:
Look yourself up online
- Look up your name and other data, such as your address, phone number, and date of birth online using all search engines.
- Use the private window or incognito mode to get a wider range of results.
- Use advanced search techniques, also known as Boolean searches, to obtain more precise results.
- Try a reverse image search with a photo of yourself to see where else it appears.
- Look up the data of family members to see what information is available on them.
- Note any information you would like to restrict or remove.
Removing or restricting data
- Remove or restrict access to information on social media sites, including images.
- Regularly review the privacy settings on your social media accounts to ensure you are happy with what data is available to the public.
- Ask family and/or friends to remove your personal data from their social media accounts.
- Take proactive steps to support family members to secure their social media accounts; for example, walk them through how to make data private.
- Review internet archive sites, such as the Wayback Machine, and follow the steps to remove your data from those sites.
- Consider blurring out your house on Google Maps and other online maps.
- If based in Europe, request that information be removed from Google under the Right to be Forgotten legislation.
- If based in the United States, sign up to a subscription service to have your data removed from data broker sites.
Other steps to be more secure
- Set calendar reminders to look yourself up online.
- Set up Google alerts for your name, including any common misspellings, as well as for other personal information, such as your date of birth.
- Secure your accounts with two-factor authentication and a long, unique password.
Other resources
More detailed information on protecting against online abuse can be found here: Resources for protecting against online abuse.
For editors interested in better protecting their staff against online abuse, please see our Editors’ checklist.
The Coalition Against Online Violence is a useful source for information for those looking to learn more. CPJ is a member of the coalition, a collection of global organizations working to find better solutions for women journalists facing online abuse, harassment, and other forms of digital attacks.
Protect your accounts
Journalists use a variety of online accounts that hold both personal and work-related information on themselves, their colleagues, families, and sources. Securing these accounts and regularly backing up and removing information will help protect that data.
Before signing up to a service
Before signing up for an online service, such as social media platforms, messaging apps, and email services, review the terms of service to find out who owns the company and where the company is based, and to understand what they are doing with your data. Understand how this could put you and your sources at risk if there is a data breach or a legal request for your data. This is especially important if you are using online services to communicate with or store data on sources, including social media, messaging apps, and interview transcribing services.
Review the transparency reports published by the technology companies you use to see which when and how they have replied to government requests to remove or hand over data.
Keep up to date with the latest information regarding the services you use. Be alert to any data breaches or changes of ownership that could indicate that the service is not as secure as it once was.
Secure your accounts
The most effective way to secure your accounts against hacking of your accounts is to turn on two-factor authentication (2FA). Two-factor authentication is an extra layer of security and is now offered by most online services. Turn it on for all your accounts where possible.
There are several forms of 2FA, and journalists should consider using an app, such as Authy, instead of SMS as their form of 2FA. Those at high risk of hacking should consider using a security key, such as a YubiKey.
All online services offering 2FA should also offer backup codes to use in case you are unable to access the account using your form of 2FA. These are one-time use codes that you can submit instead of receiving a code to your phone or app. Ensure you keep a copy of these backup codes. You can print them out and store them somewhere safe or keep them in your password manager.
In addition to 2FA, create long passwords of more than 16 characters. These should be a mixture of numbers, symbols, and letters. Do not reuse passwords or include in your password personal information that can easily be found online, such as your date of birth.
Consider using a password manager to help you manage your passwords. Research all password managers to see which is the best fit for you. Create a long unique password for your password manager.
Manage the content in your accounts
- Think about what information is stored in each account, and what the consequences would be for you, your family, and your sources if your account is breached.
- Separate your work and private life online and avoid mixing professional and personal information in accounts. This will limit access to data if one of them is breached.
- Review your privacy settings and understand what information is public, especially on social media. Remove or make hidden any data you do not want seen by others.
- Create backup copies of any information that is sensitive or that you would not want made public, including private messages and emails, then delete them from your account or device. Third party tools are available to help you encrypt individual documents to store on an external drive or in the cloud. It is also advisable to encrypt external hard drives. Review the law with regards to encryption where you are based.
- Delete any accounts that you no longer use. Remember to create copies of any information you want to save. Erase all information from the account before permanently deleting it.
- Check to see if any of your accounts have been involved in a security incident by looking them up on have i been pwned. If you find that an account you opened has been breached then you should log into that account and change your password. If you no longer want to use that account then you should delete all content before deleting the account.
- Create long passwords of more than 16 characters. These should be a mixture of numbers, symbols, and letters. Do not reuse passwords or include in your password personal information that can easily be found online, such as your date of birth. Consider using a password manager to help you manage your passwords. Research all password managers to see which is the best fit for you. Create a long unique password for your password manager.
- If you are at risk of detention or you are worried about unauthorized access to your devices, log out of accounts after each use and clear your browsing history.
- Regularly review the “account activity” section of each of your accounts. This is normally found in the “settings” section. This will reveal if devices you don’t recognize are logged into your accounts. If a device you don’t recognize is logged in then you should immediately log your account out of that particular device. You may wish to take a screenshot for your own records before logging out.
- Avoid accessing your accounts on shared computers, for example, at an internet cafe. If you have no choice, log out immediately afterwards and erase your browsing history.
Protect against targeted phishing attacks
Journalists often have a public profile and share their contact details to solicit tips. Adversaries looking to access journalists’ data and devices can target them – or a colleague or family member – with phishing attacks in the form of tailored email, SMS, social media, or chat messages designed to trick the recipient into sharing sensitive information or installing malware by clicking on a link or downloading a file. There are many types of malware and spyware which range in sophistication, but the most advanced can grant a remote attacker access to the device and all of its contents.
To defend against phishing attacks:
- Research the tech capabilities of your adversaries to understand the threat and the likelihood you or someone you know could be a target.
- Be wary of messages that urge you to do something quickly or appear to be offering you something that appears too good to be true, especially if they involve clicking on a link or downloading an attachment.
- Check the details of the sender’s account and the message content carefully to see if it is legitimate. Small variations in spelling, grammar, layout, or tone may indicate the account has been spoofed or hacked.
- Verify the message with the sender using an alternative method, like a phone call, if anything about it is suspicious or unexpected.
- Think carefully before clicking on links even if the message appears to be from someone you know. Hover your cursor over links to see if the URL looks legitimate.
- Preview any attachments you receive by email; if you do not download the document, any malware will be contained. If in doubt, call the sender and ask them to copy the content into the email, or take screenshots of the document in preview instead of downloading it.
- Be cautious of links or documents sent via group chat. Chats with large numbers of people in them may be infiltrated by the authorities or criminal groups looking to target participants.
- Use the desktop version of apps to review messages and links if possible. A bigger screen helps you verify what you have received, and you’re less likely to multitask.
- Upload suspicious links and documents to Virus Total, a service that will scan them for possible malware, though only those that are known.
- Enable automatic updates and keep all software on your devices up to date. This will fix known vulnerabilities that malware relies on to compromise your security.
- Ensure you have two-factor authentication turned on for all your accounts. This will ensure that if your password is stolen, adversaries will find it more difficult to access your account.
- Stay particularly alert to phishing attempts during elections and periods of unrest or if colleagues or local civil society groups report being targeted.
Device security
Journalists use a wide range of devices to produce and store content, and to contact sources. Many journalists, especially freelancers, use the same devices at home as well as at work, potentially exposing a vast amount of information if the devices are lost, stolen, or taken. Journalists should encrypt computer hard drives, phones, tablets, and external storage devices, especially if they travel or are at high risk of having their devices seized, to ensure that others will not be able to access this information without a password.
Best practices to secure your devices
Encryption
- Activate encryption for your computers. Mac users can enable FireVault, and Windows users can turn on Bitlocker. For Linux operating systems, turn on LUKS.
- Before encrypting your computers, create a long password that is not used on any other account or device. This password should be at least 15 characters long and include a mixture of numbers, symbols, and letters, or a collection of words that are unrelated to each other.
- Since 2014, iPhones have been encrypted by default. Android users will need to turn on encryption. This can be found by going to the settings sections and then to security>encrypt phone.
- Be aware that someone with knowledge of your password or the power to compel you to decrypt your device will be able to look at the information. This can include law enforcement.
- Always research the law to ensure encryption is legal in the country you are living in or traveling to.
- Lock devices with a password or PIN. Longer PINs or passwords are more secure. If you are crossing borders or are concerned about having your devices seized and searched, turn off biometrics.
- If you are at high risk of being targeted by sophisticated spyware and are using Apple devices with the latest operating system, consider turning on Lockdown Mode. You will need to turn it on for all Apple devices linked to the same iCloud account to ensure full protection.
- Power down and turn on your devices to reboot them. Do this regularly if you are concerned about spyware infections.
- Turn off your devices at night or during periods where they are not being used, especially if you are concerned about them being seized by the authorities. Powering down your device enables encryption and once restarted will require a password to unlock.
- Update your operating system, apps, and browsers when prompted. Old software has vulnerabilities that can be exploited to install malware on your devices. This is especially important if you feel you may be targeted by sophisticated spyware.
- Audit the information stored on your devices and consider how it could put you or others at risk.
- Regularly delete sensitive information, including chat messages. To prevent an adversary from restoring deleted files, use secure deletion software to wipe the device, if available; otherwise reset it and use it for unrelated activities in order to rewrite the device memory. (Back up anything you want to keep first or you will lose all your data.) Be aware that governments and others with specialist IT support may be able to recover content that has been erased.
- Back up your devices regularly in case they are destroyed, lost, or stolen. Encrypt and store the backup copies, ideally on an external hard drive, away from your regular workstation or home.
- Be aware that your device may back up your data to the cloud account linked to the phone. Information stored in the cloud may not be encrypted. You can turn off automatic backups in the settings.
- Don’t leave devices unattended in public, including when charging, as they could be stolen or have malware installed on them.
- Don’t use USB flash drives that are handed out free at events. These could come loaded with malware that could infect your computer.
- Consider setting up your devices to allow you to wipe any data remotely. This feature must be set up in advance, and the device will only wipe if it is connected to Wi-Fi or cellular data. If your devices are stolen or seized by others, they may turn on airplane mode, preventing the device from being wiped. Be aware that wiping your devices remotely can come with legal repercussions.
- Always get devices repaired with a reputable dealer.
Encrypted communications
Journalists can communicate with sources more securely using encrypted messaging apps or software that encrypts email so that only the intended recipient can read it. Encryption protects the content of messages, but the companies or organizations involved may be able to see the metadata, including when you sent the message, who received it, and other revealing details. Companies have different policies on what data they collect, how they store this data, and how they respond when authorities ask for it.
Recommended messaging apps offer end-to-end encryption by default, meaning that encryption does not have to be turned on by the user and that the information is encrypted when it is being sent from the sender to the recipient. End-to-end encryption means that information is also encrypted on the server of the company or organization, meaning that it cannot be legally subpoenaed. Be aware that anyone with access to a device sending or receiving the message or to the password of the account linked to the app can still intercept the message content. Examples of messaging apps with end-to-end encryption turned on by default include Signal and WhatsApp. Other apps may require you to turn on end-to-end encryption.
Metadata
Metadata is not the content of your communications, but the data linked to them. Examples of metadata include phone numbers, time stamps, and the duration of a call, among others. Metadata can be used to create a picture of who you communicate with. This information is often not encrypted and can be subpoenaed by law enforcement. If you are concerned about metadata, then you need to use an encrypted messaging service that collects as little data as possible.
Best practices for using end-to-end encrypted messaging apps
- Research who owns the app, what user data they keep, what metadata they have access to, and whether that data has been subpoenaed by a government. Check to see what their policy is for responding to requests to share user data. Tech companies should produce a transparency report each year covering government requests to remove or share data.
- Back up and delete messages regularly to store as little as possible on a single device or account. Create a process for reviewing content, including documents and multimedia messages, and store downloads or screenshots on an encrypted external storage device. Be aware that these messages may exist in the account of the person you sent them to.
- Understand where information sent to your messaging apps, such as photos or documents, is stored on your phone. Anything you download, like photos, will be saved on your device and may be copied to other devices and apps, especially when you back up your data.
- Contacts stored in your phone sync with messaging apps and cloud accounts, so numbers you try to delete in one place may be preserved somewhere else.
Advanced features for end-to-end encrypted messaging apps
- Lock the app with a PIN or passcode where possible to better protect against someone opening the app if they have physical access to your phone.
- Set up a registration lock, if the service offers one, to require anyone installing the app with your phone number to enter your PIN number.
- Protect your phone number by creating a username for your Signal account. Give out your username instead of your phone number.
- Some apps, including Signal and WhatsApp, provide an extra security step to verify who you are chatting with and prevent someone impersonating one of your contacts from another device. Look for the option to verify safety number or security code in the app settings.
- Some services, like WhatsApp, back up your message content to the cloud account linked to the telephone number. You can turn on encryption for the cloud backup in the settings section of the app. Create a long and unique password for that backup. If you do not want to create a backup, you can turn off this option in the settings section. Be aware that if you uninstall the app and install it later, you will lose all the content stored within the app, including messages. For iOS users, be mindful that your call history on Signal syncs with iCloud. You can turn this off in the app settings.
- Disappearing message functions on Signal and WhatsApp allow you to automatically delete messages after a certain time. Turn these on if you are concerned about your phone being taken and your messages being accessed.
- Both Signal and WhatsApp offer the possibility to set photos and videos to delete after viewing them. It may be helpful to turn that on if you are sending sensitive images.
- Signal and WhatsApp also offer end-to-end encryption for video calling.
- If you are concerned about spyware attacks on your WhatsApp account, you should enable the WhatsApp security feature Strict Account Settings.
Best practices for using encrypted email
Using an encrypted email service is another way of ensuring that your communications are secure. There are a number of encrypted email providers that journalists can use. Some of these providers also offer other encryption services, such as cloud storage, calendar, and contacts. Examples of encrypted email providers include Proton Mail, Tuta Mail, and Mailvelope for Gmail.
If you are using an encrypted email service and sending an email to someone who is using the same service, the contents of that message will be encrypted automatically. If you need to email someone using a different email service, then you will have to turn on encryption, requiring the other person to use a password to open the email. It is important to bear in mind that even though your emails are encrypted, the service provider may still hold the metadata, including the subject of the email and the address of the receiver, among others. Review the terms and conditions carefully to understand what data is and is not encrypted.
Using the internet more securely
Journalists rely on the internet for carrying out research, which can leave them and their sources vulnerable if they do not take steps to protect themselves. Internet service providers, governments, companies, and criminals collect data on internet users which can be used to target them, including building legal cases against them.
To use the internet more securely:
- Research who owns your internet service provider (ISP) and what the company’s legal obligations are with regard to passing your data to governments, including your own. Look to see what data they store on you and for how long.
- Protect your browsing history from your ISP by using a virtual private network (VPN). Be aware that your ISP will log that you are connected to a VPN service, which could be an issue if VPNs are illegal in your country. Ensure you choose a VPN that does not track and record your browsing history as this can be shared with governments and others. Choose a VPN service founded and located in another country as this can make it more difficult for your government to obtain your data.
- Most websites are now encrypted, which means that while people may be able to see you are looking at a website or logged into an online service, they will not be able to see the content of that page. Look for https and a padlock icon at the start of every website URL (https://cpj.org), indicating that traffic between you and the site is encrypted. DuckDuckGo Smarter Encryption is a tool that better ensures that the site you are visiting is encrypted.
- When you visit a website, it collects data on you, including your IP address, which gives away your approximate location; details about your device, including the operating system; and your time zone among others.
- Install an ad-blocker to protect against malware, which is often hidden in pop-up advertising. Ad-blockers allow you to exempt certain sites from being blocked, including your own media outlet.
- Install Privacy Badger to block websites and advertisers from tracking what sites you visit online.
- Consider installing the free Tor Browser Bundle to use the internet anonymously or Tails, a free operating system that routes all your internet traffic through Tor. Tor is especially recommended for journalists who investigate sensitive topics like high-level government corruption in countries with sophisticated tech capacity. Review the law with regard to using Tor in the country you are in.
- Governments, criminals, and others can create spoof websites that can be used to collect your personal data, such as passwords, and credit card details among others. Check that the website address is authentic; the URL should be spelled correctly and include https.
- If possible, avoid using public computers, especially at internet cafes or press rooms. Public computers may be infected with malware or spyware. If you do have to use a public computer, avoid logging into your personal accounts, ensure that you log out of all sessions, and clear your browsing history.
Crossing borders
Many journalists cross borders carrying work and personal information that they may not want others to access on electronic devices. If border guards take a device out of your sight they have an opportunity to search it, access any accounts, copy information, or install spyware. Journalists crossing U.S. borders should consult CPJ’s safety note, “Nothing to Declare.”
Before you travel:
- Find out what information is on your devices and how it could put you and your contacts at risk. Assume your devices could be subject to the same level of scrutiny as notebooks and printed material in your luggage.
- Back up all your devices to an external hard drive or to the cloud. Remove any information that you would not want border officials to access from your devices.
- Buy clean devices to use only for travel if possible, especially if you are working on highly sensitive stories. If you are traveling with a personal or work device, securely back up your content then perform a wipe or reset.
- Turn on full-disk encryption for all devices to ensure that your information cannot be accessed without a password. Research restrictions on encryption of the country you are visiting to ensure you are not breaking any laws. Be aware that security forces may legally be allowed to ask for your password. Seek advice from your employer or lawyer before travel if there is a possibility you will be stopped at the border.
- Log out of all accounts on your devices and uninstall apps until you have crossed the border and reached a secure Internet connection.
- Clear your browsing history on all your devices. (Your internet service provider and browser will still have a record of which websites you have visited.)
- Lock all devices with a PIN or password instead of biometric data like your face or fingerprint.
- Enable remote wiping of your devices and leave clear instructions with someone you trust to wipe your devices remotely if you are detained. Devices will only remote wipe if they are connected to the internet.
At the border:
- Power off your devices to activate disk encryption.
- Keep an eye on your devices as they pass through security.
- Be aware that any SMS messages or phone calls that are not end-to-end encrypted will be routed through a local service provider who may collect the content or share it with authorities.
If any device is confiscated at the border or anything is inserted into it, assume it is compromised and that any information on it has been copied.
Editors’ note: This kit was originally published on July 30, 2019, and reviewed for accuracy on the date shown at the top.